This week, the Democratic National Convention met in Philadelphia. Most people anticipated a big history-making announcement on Thursday. It was an announcement the weekend before that got much attention. Some consider the amount of physical security that goes into protecting a candidate and question how their cybersecurity can be so weak. Perhaps this would lead people to wonder how secure anything is. Could their personal information get leaked out on the black market because they paid their bills online? Your customers demand a secure payment solution.
Politically, we live in an exciting time. No one knows that more than members of the Democratic National Committee. Their servers fell prey to hackers a few months ago. This exposed private emails, opposition research, and campaign correspondence. Nearly 20,000 of those private emails got leaked to the public and revealed embarrassing details of the political machine’s inner workings. U.S. cyber-security experts have reason to believe Russia was responsible for stealing the DNC materials, and the FBI suspects Russia may have had political motivations. If this is true, this would be quite reminiscent of the Watergate Scandal from the 1970s
The Importance Of Security
 To protect the national and economic security, the White House approved a Presidential Policy Directive (PPD) on United States Cyber Incident Coordination. This directive would allow the Government to improve the capabilities necessary to prevent and protect against, cyber-attacks. President Obama has consistently emphasized that malicious cyber activity poses a serious threat to the national and economic security of the United States, and has worked to prevent such attacks in the last seven years.
To protect the national and economic security, the White House approved a Presidential Policy Directive (PPD) on United States Cyber Incident Coordination. This directive would allow the Government to improve the capabilities necessary to prevent and protect against, cyber-attacks. President Obama has consistently emphasized that malicious cyber activity poses a serious threat to the national and economic security of the United States, and has worked to prevent such attacks in the last seven years.
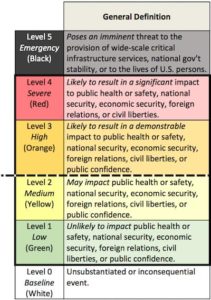
Cyber Incident Severity Schema
The White House also issued the U.S. government’s first emergency response manual for a major cyber-attack. Called the Cyber Incident Severity Schema, it is a color-coded scale that would allow government entities to know how to evaluate the level of a cyber-threat properly.
The Cyber Incident Severity Schema has various ranges. The lowest is white, or an “unsubstantiated or inconsequential event.” The highest is black, or an attack which poses a threat to critical infrastructure services, national government stability, or to the lives of U.S. persons”. Between the two are green, yellow, orange, and red. Any hack or threat of a hack rated at orange or above gets considered a significant cyber incident. This would trigger a coordinated response from government agencies.
Such a procedure will allow for public entities to evaluate how imminent a threat is and how to coordinate and stop it appropriately. For example, a green level security threat would require an appropriate standard of discretion. Whereas a black level event would need more immediate attention.
The Rise Of Identity Theft
Fortunately, the latest Jason Bourne movie wasn’t a documentary. The US Government hasn’t reached anything that has ranked as a high-level threat yet. However, identity theft and cyber-attacks are on the rise. Some customers may be too afraid to go online to pay for your company’s good and services. Worst yet some businesses may still insist that a paper check or money order is the best way to go. This couldn’t be further from the truth. IVR Technology offers a solution that’s easy to integrate and doesn’t put your company’s data, or the data of your customers, at risk.
The Problem With Checks
While a somewhat traditional form of payment, checks were never exactly the most reliable method. It takes time for a check to travel to a customer’s account. Also, when it comes to due dates, does that mean that the payment should arrive on that date or is the date stamp on the envelope good enough? What if the bank withdrew your customer’s funds out of sequence, or if the customer miscalculated and now they don’t have enough money in their account to cover their funds? Bounced check fees can be a real financial burden for your customer.
Not to mention your customer’s address, routing number, name, and all sorts of information are on every one of them. If their check got into the wrong hands, they could put themselves at risk.
- Here’s a story of a man that allegedly stole his grandmother’s checkbook and robbed three banks.
- These men stand accused of stealing rent checks from an apartment’s payment box.
- Even if a customer puts the check in a mailbox, thieves have managed to break the mailbox’s lock and take the checks.
Even the entity responsible for processing paper checks, the National Automated Clearing House Association (NACHA) recommends not using paper checks. A representative released this statement to Fusion online magazine, “The most efficient way for consumers to safeguard bank account numbers is to stop using paper checks. Since money transferred electronically passes through fewer hands than a paper check, electronic payments can be a safer option for consumers.”
Are Online Payments Any Better?
Online payments can be better; however, they have their problems. If the website that accepts payments is not secure, it could put your customer’s information at risk. Not to mention, customers may have full intention to pay you, but could click a link that leads them to a fraudulent website. Even if your payment website is secure, they may have malware that could wipe their bank accounts clean. Protecting sensitive data is a constant challenge because of persistent and rapidly escalating threats.
IVR Phone Payments Protect Your Customers Data
With an IVR phone payment solution, customer payments are safe. Best of all their payments get verified in minutes, so the payments get processed on time. It’s as easy as making a phone call, receiving their information, and making a payment. IVR Technology can also process payments by phone call or text message.
Considering the other nightmare scenarios covered above, it is safe?
IVR Technology Group dedicates itself to protecting your customer’s data. That’s why we built our phone payment solution, Compass Pay, with data security in mind. Our company is PCI Level 1 Compliant, the highest level of security compliance that a service provider can receive.
The Difference Is Tokenization
When a customer makes a payment, the information is immediately encrypted and swapped with a token. Tokens replace card data with a surrogate value. This value gets passed along during the transaction. Meanwhile, the real data remains safe on a secure server. Should a cyber-criminal access hack the server, they will only find the token, which does not contain any information of value.
Give Customers Peace Of Mind
There are many payment options out there, for your customers. If you want to want them to have peace of mind, go with a phone payment solution that guarantees security. Our solution, Compass Pay, will make sure your customer’s payment is confidential and secure.